Customers often ask me that they want to achieve better visibility around the following questions they have in day to day operations:
- Who (user context) is accessing applications?
- What AD groups are accessing which applications?
- What users and AD groups are communicating laterally in the campus?
- What device type accessed the application?
- What processes are running on these devices?
- What is the zero-trust policy for the enterprise and connecting to applications?
- Performance troubleshooting with user context-aware telemetry?
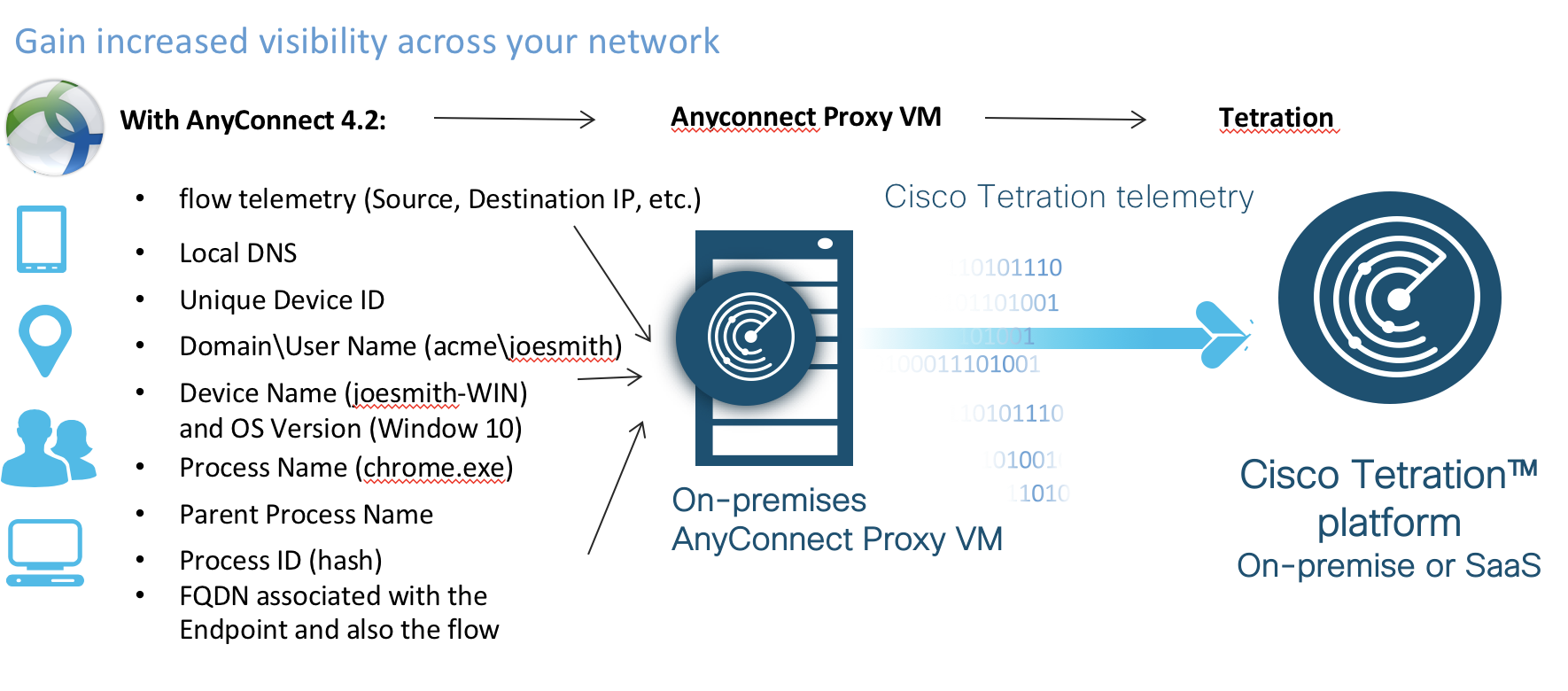
And while some tools can get you some of this data, there is nothing as comprehensive as Tetration to give you pervasive flow visibility with context. So to make Tetration even more impactful to your network and security operations, Tetration is introducing endpoint visibility using Anyconnect Client with the Network Visibility Module (https://bit.ly/2zMPqHH). That's right if you are an Anyconnect client you can enable the NVM module with no additional agent.
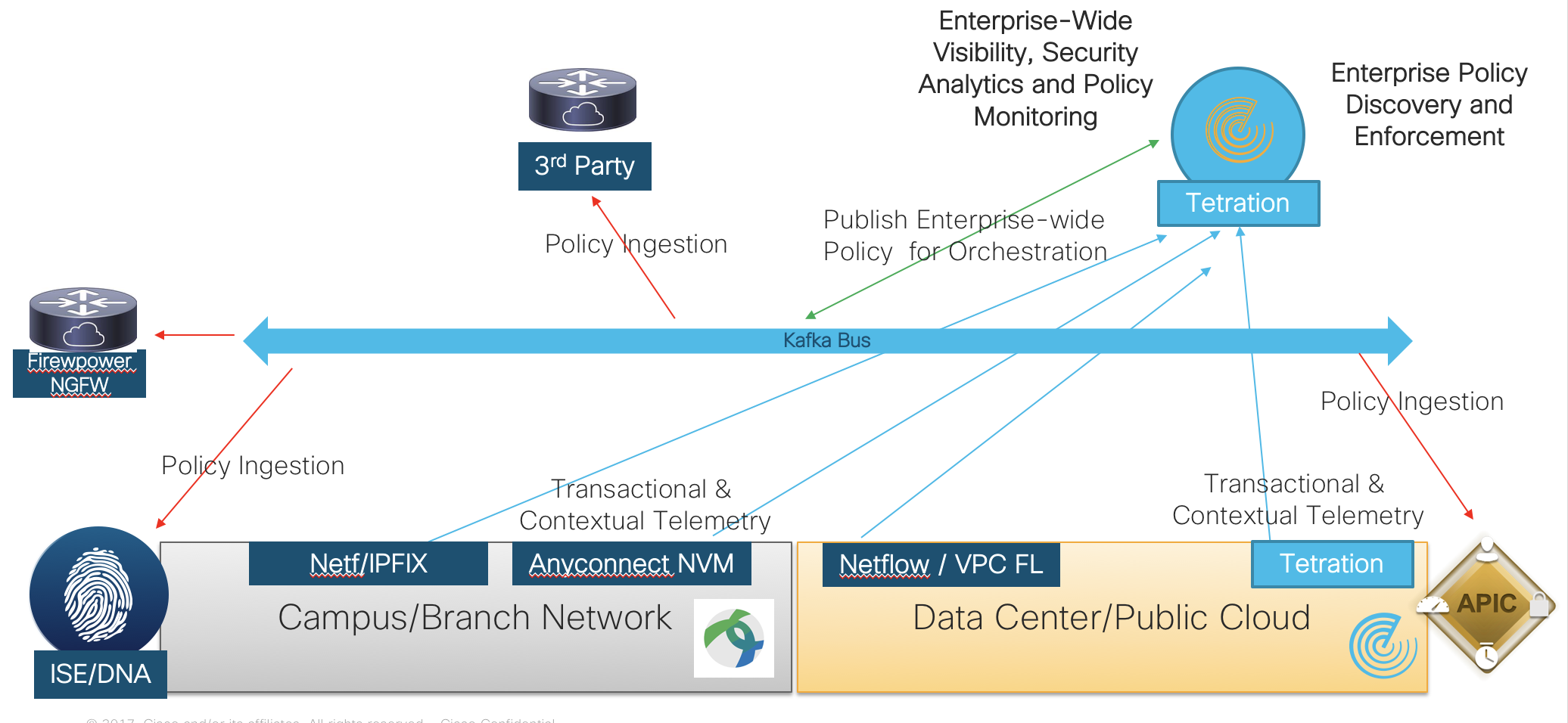
The open architecture of Tetration allows us to collect telemetry from Tetration software sensors, OOB Sensors, Hardware sensors, Netflow(v9), IPFIX, AWS VPC Flow Logs, Netscaler/F5/AVI IPFIX flow data and of course now Anyconnect NVM.
So, what will Tetration do with this new telemetry from Anyconnect NVM?
Tetration discovers user and group zero-trust segmentation policy to control access to the application workloads and lateral movement in the campus! Get to see who is accessing what, what URLs were accessed, search by user-specific flows, and much more!
Now what? Where do you deploy the end-user and discovered segmentation policy? Tetration publishes the zero-trust policy discovered to a Kafka message bus for any vendor to consume, normalize and enforce within the campus infrastructure. Think about rolling out Cisco DNA with a zero-trust policy day 1. How about having ISE ingest dynamically discovered policy from Tetration and enforcing with Trustsec? A consistent zero-trust policy across the campus, branch, WAN and wherever your application workloads exist. Don't forget Tetration will also natively enforce policy across your application workloads via the software sensor manipulating iptables and windows advanced firewall in the data center or public cloud. A consistent zero-trust policy across the enterprise is the outcome.
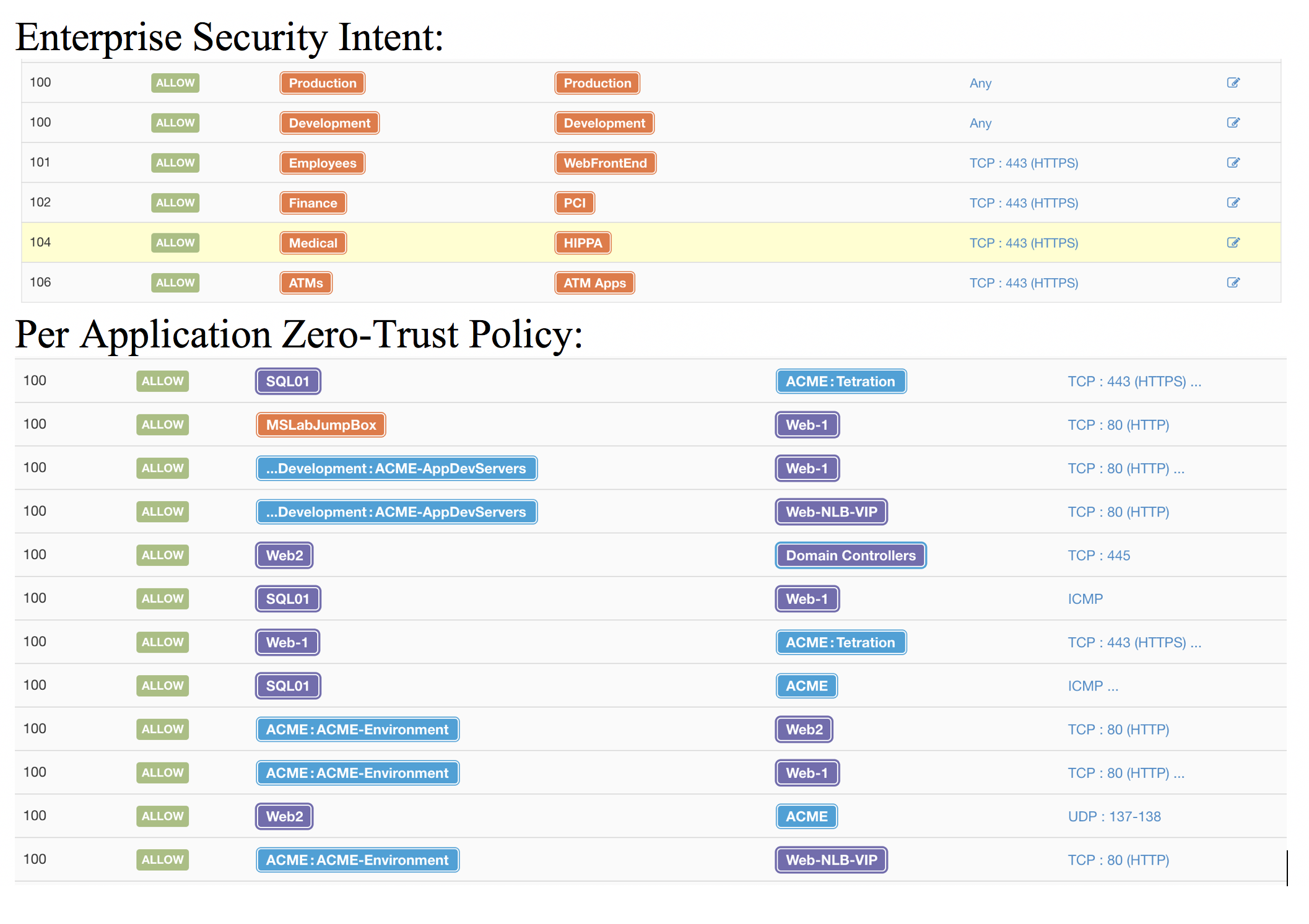
If we look at the big picture in a zero-knowledge environment, you can dynamically discover and write an intent-based hierarchical zero-trust policy for the enterprise. A policy such as:
- Allow access to "FinApp" only to users in group "Finance."
- Allow access to "HIPPA-Apps" only to users in group "Medical."
- Allow access to "ProductionApps" only to users in group "employees."
- Allow access to "DevelopmentApps" only to users in group "developers."
- Allow access to "ATM-Apps" only to devices in group "ATMs."
Hierarchically stack the intent defined above with segmentation policy dynamically discovered for each unique application, and you have an enterprise zero trust policy with cloud workload protection.
To summarize with Anyconnect NVM added as telemetry source here are new business outcomes that are achievable:
- Long-term data retention for user flows, and process forensics
- Ability to capture and tie each user and their flow(s) back to what server/application it accessed
- Better contextual information including access to the server process, clusters, and application - from the endpoint/user perspective
- Application dependencies, policy recommendation/testing, and server workload protection policy with user/group context
No comments:
Post a Comment