Mmmm… crunchy outside, gooey inside - sounds good, right? Well, if you’re talking about a piece
of candy, sure it does, but if you’re talking about your IT info-sec posture, it’s
not hard to argue it’s just going to make you sick.
If you look at the headlines over the past few years, there
is nothing more eye-catching than the millions of customer records that have
been compromised due to a known vulnerability. Apache Struts got a lot of press
recently and perfectly illustrate this type of activity.
Anatomy of a Compromise
What’s fascinating to know about this is the way the data
loss happened. Typically, the valuable data rarely lives on the systems that
get compromised due to this type of vulnerability, but rather on disparate
systems that may or may not be associated with the system that is vulnerable. The
way this works, especially in the example of the well-publicized Apache Struts
compromise, is somewhat like this: there is a bug in some code (Struts) that
allows a remote attacker to send a specifically designed message to the server
and that allows direct access with
escalated privileges. The great thing about this from the attacker’s point of view is
that it looks like just regular connections from a port/protocol perspective, so
many tools won’t see the difference. Of course, the connection characteristics
are different, but this type of differential is challenging to get
visibility into.
Once the attacker who now has admin rights to the compromised
box can start probing the internal network to see if there are high-value
systems that they could get information from. It’s not difficult once someone
has admin control to load some scanning programs and start digging for well
known ports like possibly mySQL or SQL Server or something like that. If there
are no digital walls inside an infrastructure, its not hard to see how quickly
one edge compromise can lead to an amplified risk to all other elements in the
rest of the infrastructure. This is like breaking open the candy to get to the
good, gooey center…
Think about it… when you go to a hotel, you would prefer a
hotel that has keys for every door, or just one key to get into the elevator?
If the one-key-per-door approach didn’t exist, all you would have to do is get
in and you could do anything you wan where ever you want. That is what you’d
call a “bad thing”.
Make All the Things “More Crunchy™”
So… we can see how one small crack in the outer shell can
allow someone to get to all the gooey goodness, so how can we get around this?
Edge or perimeter defense is where most people spend almost
all of their time securing workloads. That’s good… but as you can see from the
gooey center, it’s not enough. The trade off is that if you provide
perimeter-like defense for every server and service inside an infrastructure,
you will be doing a massive amount of “unnatural things”, such as policy-based
routing to ping-pong traffic to firewalls and things like that… but that can increase
complexity in a significant fashion and therefore increasing fragility, which
is never good. It is possible to do this, but it’s not an easy thing to do, and
being able to do it with confidence takes a significant amount of visibility
and knowledge, and would also require a significant amount of automation to
execute the rules. If all of that can be done, you will also still have to deal
with hardware limitations in asics/tcam tables for rules storage and execution.
Basically, this is putting a really large amount of strain on a set of boxes
that are not really designed for this level of granularity, so that would mean a
company’s investment in the size and number of boxes to satisfy this need would
be extremely unwieldy.
Why Tetration
What Tetration is built to do is to decrease risk and
increase efficiency of building a defense in depth strategy through these high-level
intents:
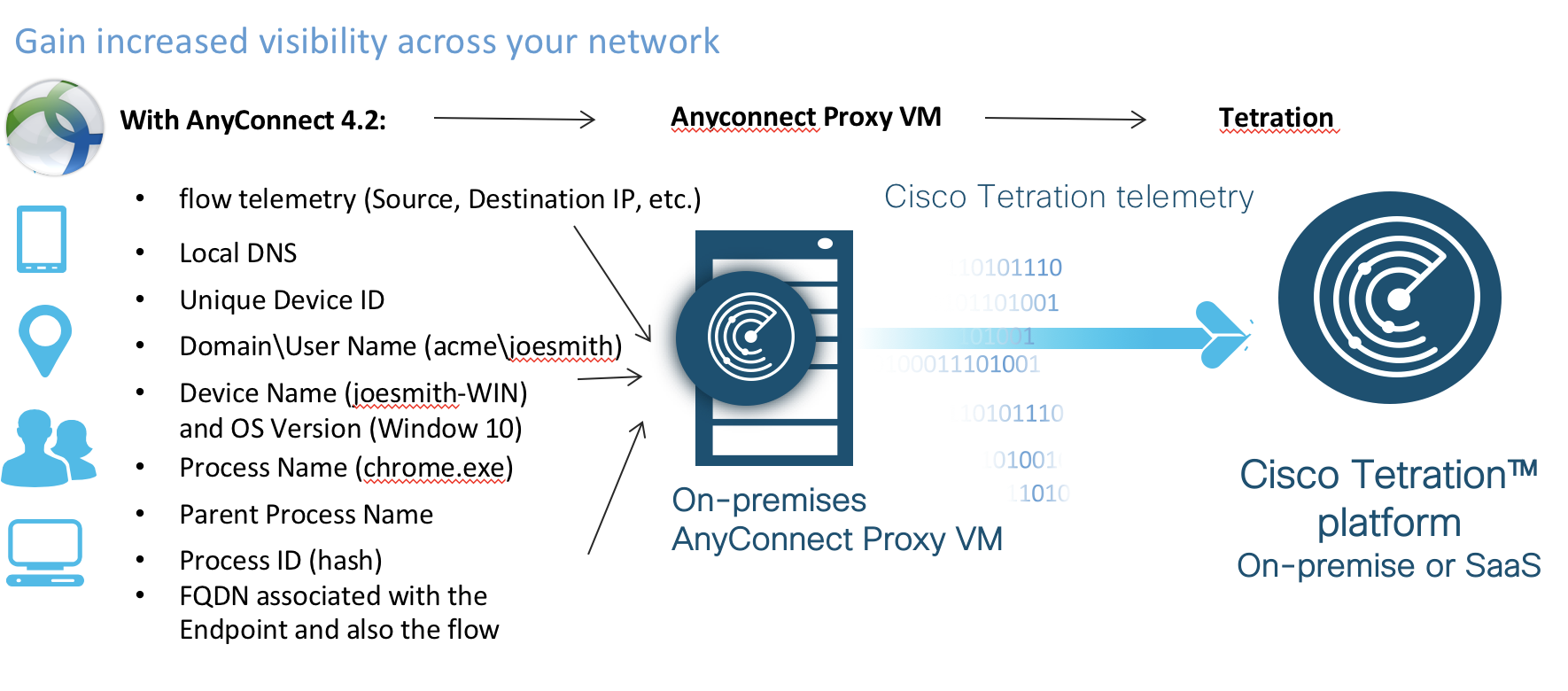
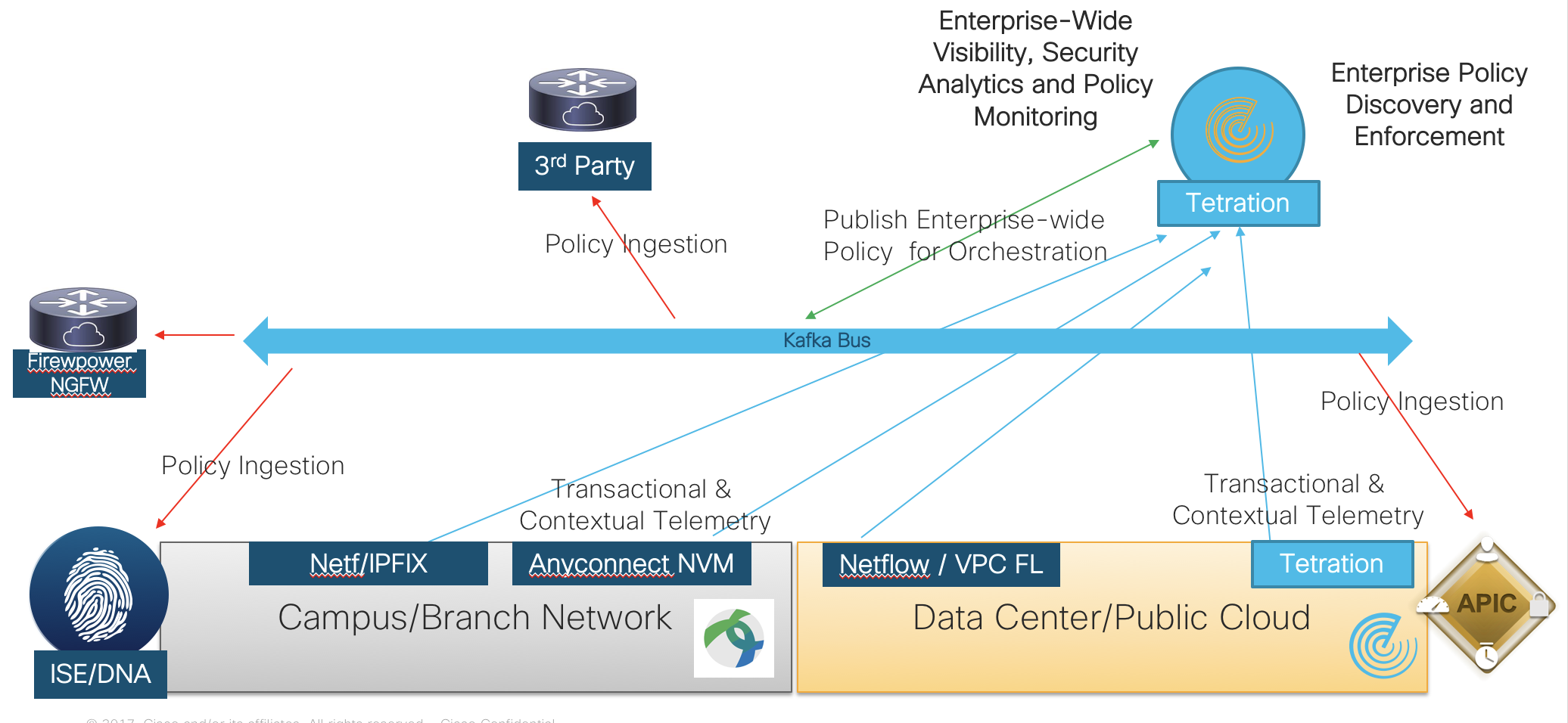
- Visibility
- By utilizing sensors on servers, virtual machines
and in the network, Tetration can increase visibility down to being able to
gather meta data for every packet for every flow inside a DC, in any cloud deployment, as well as data
on system integrity and software vulnerabilities
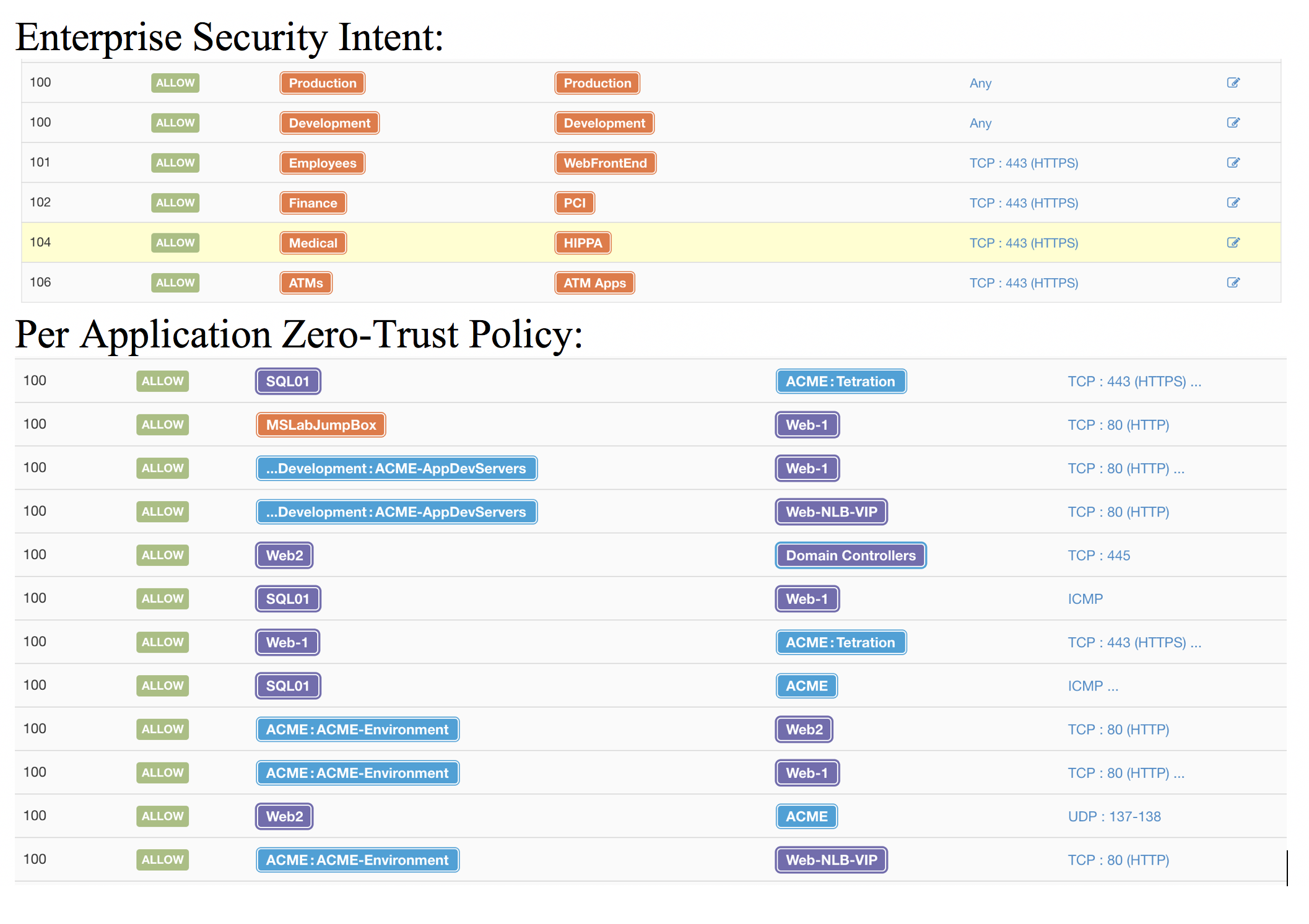
- Understanding
- Tetration uses the data from all of the sensors
and applies machine learning algorithms to build application dependency
mappings, which provides a policy list that can be applied to create the walls
between the application tiers and even between the workloads within the tiers
- This data can be used internally through native
protection (see next bullet) and can be exported manually or programmatically for
use in other protection mechanisms (i.e. fw, acl, aci contracts/filters, etc.)
- Protection
- Systems instrumented with the Tetration software
sensors can do native policy enforcement based on the application dependencies that
have been discovered
- Tetration does software inventory checks against
a robust CVE database which allows identification protection mechanisms against
vulnerable software. In the example above, we could write a rule that says “anything
with the apache struts vulnerability cannot talk to production or internet, but
can talk to our patching servers”
- Tetration watches process behavior in the kernel
and will report and record process anomaly events, such as privilege escalation
and shellcode execution (two of which were used to crack into the candy shell
above), as well as other kernel events, such as socket creation, side channel
attack, file access, binary changes, and others.
Same Candy, More Crunch
With the tools that Tetration is able to bring to bear, we
have the ability to deliver unprecedented understanding of what is going on in
the infrastructure as well as new tools to protect the security zones inside
the perimeter, providing protection against unwanted lateral movement as well
as mechanisms to see vulnerabilities and kernel process abnormalities in ways
not seen before.
In other words, with Tetration, it’s the same candy with
WAY more crunch.
Give me MORE!
If you'd like to learn a little more about all the good stuff Tetration can help you with, please
go check out our lightboard series on Tetration!
Thanks!